Railway
Operation passage door of high-speed railway protection fence
Refined management solution

Background
Accidents related to protection fences occur frequently, and the management of operation doors cannot be ignored.
-
Two construction workers climbed the railway protection net and entered the railway line under the instruction of the person in charge, and were dealt with on the spot by the police of Jianshi Railway Station Police Station of Xiangyang Railway Public Security Department.
-
Entering through the breach of the railway line protection fence illegally and walking on the railway line, colliding with a running train, resulting in 3 deaths.
Current situation
The traditional door locks of high-speed railway protection fence do not have the functions of waterproof, anti-prying and anti-theft opening, and fail to meet the requirements of "changing from outside to inside and from exposed to hidden" of the head office.
Regular inspections cannot be supervised in place, and the rust and damage of the locks are only known after the incidents occur.
Project framework
-
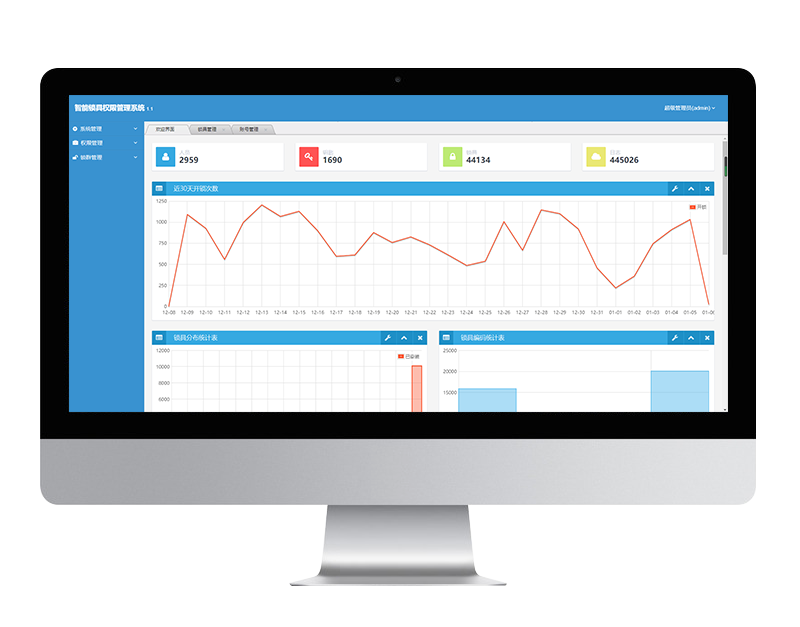
Cloud management platform
The platform centrally manages personnel, keys, locks, and the opening and locking permissions of the keys held by authorized personnel. It reads key information and relevant opening and closing records of locks in real time. Big data visualization for statistical analysis and monitoring. -
Mobile phone mini program
Functions such as lock management and positioning, applying for or receiving tasks, executing tasks, reporting abnormalities, inspecting, approving, monitoring, and statistical data, etc. -
Intelligent NB Iot electronic key
Physical intelligent key, obtaining platform tasks by authority, time, and personnel, unlocking and automatically uploading operation logs internally. -
Passive electronic lock
Passive, waterproof, anti-theft, and anti-prying. The main material of the lock cylinder is stainless steel 304. It is an electronic lock cylinder with a built-in control chip and electric drive part, automatically identifying the switch personnel. Various specifications and models of locks are suitable for various scenarios.
Solution: Cloudmanagement platform
-
System workbench
with tree structure management being clear at a glance. -
Lock management
combining the list and map presentation methods to make each lock clearly visible -
Department management
structured organization management -
Read data
Put the key on the card issuer to easily read the data. -
Key management
set the unlocking permission and time limit for each key, set the period for taking out and returning, and bind the users at the same time. -
Switch records
The records of opening and locking are clear at a glance.
Solution: NB-IOT Key

1.Identity recognition
The key has the function of effectively identifying the identity of the user, preventing the key from being illegally duplicated when lost and illegally unlocked, and protecting the rights and interests of the key holder.
2.Recording function
The intelligent key itself can record operator information, the start and end time of the switch lock operation, and the lock information, etc.
3.Remote transmission
Using NB-IoT communication and Bluetooth communication, it can automatically upload the switch lock information or remotely monitor the switch lock operation through the mobile phone.
4.Key security
If the key is lost, the following solutions are available:
1. The key authorization can be deleted on the management platform.
2. The key can be deleted on the management platform.
Solution: Passive smart lock

Technical functions
1、Eliminate technical unlocking: Adopt digital coding technology and encrypted communication technology;
2、No mutual rate: 64*8-digit coding, the mutual rate is zero;
3、With switch lock records, switch lock must be operated with a key;
4、The lock cylinder stores 22 operation (unlocking, locking, patrol, etc.) logs.
Technical parameters
1、Main material of the lock body: 304 stainless steel
2、Voltage: 3V - 5.5V
3、Working temperature: -40~80℃
4、Working humidity: 20% - 98%
5、Switching times: 300,000 times
6、Storable logs: 22 items
7、Protection level IP67
Solution: Rim lock

1.Technical functions
1、Eliminate technical unlocking: Adopt digital coding technology and encrypted communication technology;
2、No mutual rate: 64*8-digit coding, the mutual rate is zero;
3、With switch lock records, switch lock must be operated with a key;
4、The lock cylinder stores 22 operation (unlocking, locking, patrol, etc.) logs.
2.Technical parameters
1、Lock body main material: 304 SUS
2、Voltage: 3V - 5.5V
3、Working temperature: -40~80℃
4、Working humidity: 20% - 98%
5、Switching times: 300,000 times
6、Storable logs: 22 items
7、Protection level IP67
3.Scene description:
Used in the emergency evacuation passage of the bridge.
The lock can be unlocked with an authorized electronic key from the outside;
In an emergency inside, simply rotate the knob to unlock.
Solution: Phone mini program
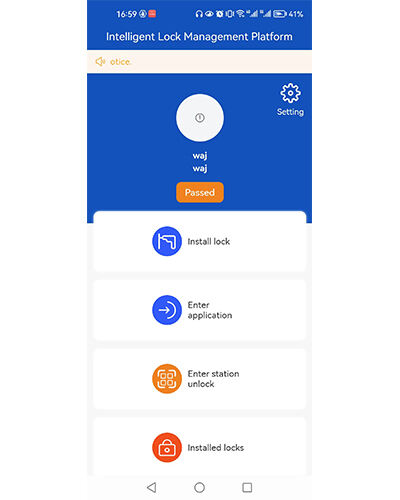
Convenient and fast
No installation is required and it is suitable for various types of mobile phones
Task application
Initiate task application processing based on the inspection status.
My devices
Showing the maintained devices of the operators in a tree structure
Operation records
Clearly display the operation logs of the locks.
Product advantages
-
Task management
Set the unlocking area, period and operation authority for on-site operators according to the needs of on-site work, remote unlocking and remote upgrade. -
Personnel management
Management of information of system administrators and on-site operators, and authority setting. -
Log management
View, count and output self-check logs and operation logs. -
Lock management
Lock group information, lock files, and hierarchical management of locks. -
Alarm information
View alarm information related to locks and tasks. -
Key management
Key files, key status management, task download.
Convenience
-

There is a big bunch of keys, and finding the right one is also a difficult problem.
-

-
"One Key Pass", convenient for unlocking
Security
-

If a key is lost, there is a security risk. All the keys need to be replaced if one is lost.
-

-
If the key is lost, the following solutions are available:
1. The key authorization can be deleted on the management platform.
2. The key can be deleted on the management platform.
Refinement
-

Manual ledger registration is prone to loopholes, making it difficult to track and manage the unlocking time, and the operators are uncontrollable.
-

-
1. Assign tasks, time, and personnel, and authorize staff to switch on and off at each level;
2. Relevant logs are stored in the cloud for real-time viewing and easy tracking.
Visualization
-

The person who unlocked the lock / The time of unlocking cannot be known.
-
-
The person who unlocked the lock / The time of unlocking are clear at a glance.
Tasks, inspections, lock status, etc. can all be remotely monitored.
GPS positioning / navigation
-

The protective fences are scattered along the railway at various locations. During the processes of operation and maintenance inspection and equipment emergency repair, a lot of time and energy are needed to find the specific locations.
-

-
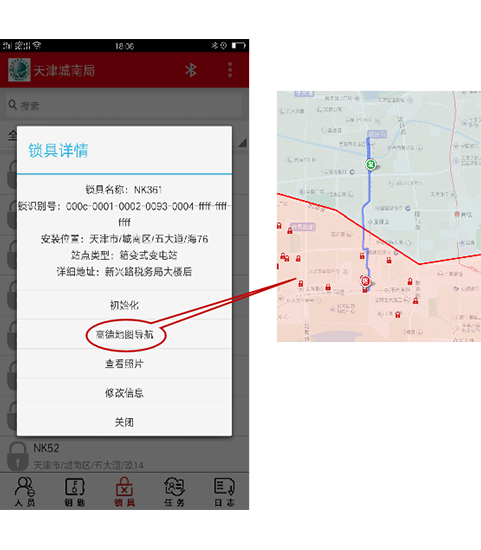
The mobile phone mini-program has the GPS navigation function, which enables the staff to arrive at the designated site at the first time, greatly saving the time for finding the station and improving work efficiency.
 EN
EN
 AR
AR
 BG
BG
 NL
NL
 FI
FI
 FR
FR
 DE
DE
 HI
HI
 IT
IT
 JA
JA
 KO
KO
 NO
NO
 PL
PL
 PT
PT
 RO
RO
 RU
RU
 ES
ES
 SV
SV
 CA
CA
 TL
TL
 ID
ID
 SR
SR
 UK
UK
 VI
VI
 TH
TH
 TR
TR
 FA
FA
 AF
AF
 MS
MS
 GA
GA
 CY
CY
 IS
IS
 AZ
AZ
 BN
BN
 LO
LO
 LA
LA
 SO
SO
 MY
MY
 KK
KK
 UZ
UZ