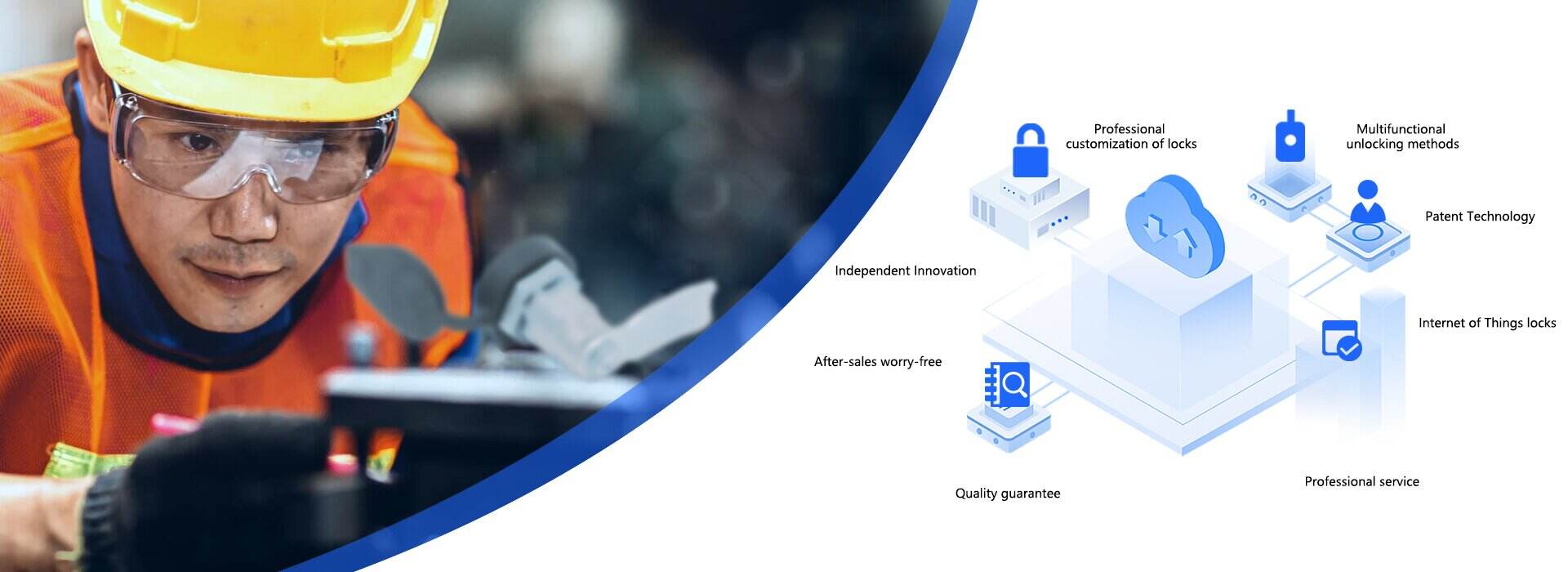
ရထားလမ်း
အောက်ပိုင်းရထီးလမ်းကြောင်း ကန့်သတ်ချိုးဖြာခံအတွင်းရှိ လှုပ်ရှားခြင်း ဖြစ်သည်
တိကျသော ဆော့ဖ်ဝဲရှင်းပြီး ဖြေရှင်းချက်

နေရာခြင်း
ကန်မှုန်းခြင်းအတွက် ပံ့ပိုးချိုးဖြေရာတွင် မှားယွင်းမှုများ မကြာခဏဖြစ်ပေါ်လာပြီး လှေချိုးဖြတ်ခြင်း၏ စီမံခန့်ခွဲမှုကို မေးမြန်းခြင်း မဖြစ်ရပါ။
-
သူငယ်ချင်းနှစ်ဦးသည် အရာရှိ၏ အမှန်တော်ကြီးမှုဖြင့် ရထီးလမ်းကြောင်းကန့်သတ်ချိုးဖြာကို တက်ရောက်ခဲ့ပြီး ရထီးလမ်းကြောင်းသို့ ဝင်ရောက်ခဲ့သည်၊ ထို့နောက် ဆိုင်ရာရထီးဘူတာရဲတပ်ချူး၏ ဂျီဃန်းရဲသီးချိန်ရှိ ရဲသားများမှ တိုက်ခိုက်ဖြင့် ပြုလုပ်ခဲ့သည်
-
ရထီးလမ်းကြောင်းကန့်သတ်ချိုးဖြာကို မှန်မှန်တိုက်ခိုက်၍ ဝင်ရောက်ခြင်းနှင့် ရထီးလမ်းကြောင်းပေါ်တွင် လှုပ်ရှားခြင်း၊ လှုပ်ရှားနေသော ရထီးတစ်စီးနှင့် ထိတွေ့ခြင်း၊ သေဆုံးသူ သုံးဦး
လက်ရှိအခြေအနေ
အောက်ပိုင်းရထီးလမ်းကြောင်းကန့်သတ်ချိုးဖြာများ၏ ကျောက်လှမ်းများသည် ရေကို ကာကွယ်ရန်၊ ဖိတ်ခြင်း၊ လှုပ်ရှားခြင်းနှင့် လှုပ်ရှားခြင်းကို မရှိပါ၊ ထို့အပြင် အဓိကို အတွင်းမှ ပြောင်းလဲခြင်းနှင့် များသော အချိုးအစားများကို ပြောင်းလဲခြင်း၏ လိုအပ်ချက်များကို မကောင်းမွန်ပါ
မှီခိုမှုများကို မှီခိုသော အချိန်များအတွင်း မှီခိုမှုများကို မပြုလုပ်ပါ၊ ကျောက်လှမ်းများ၏ ကျောက်သွားခြင်းနှင့် ကျောက်သွားခြင်းများကို အခြားအခါများတွင်သာ သိရှိရန်
ပရောဂျက်ဖောင်ဒိုင်
-
ကုမ္ပဏီ မိုးရောင်းစီမံကိန်း
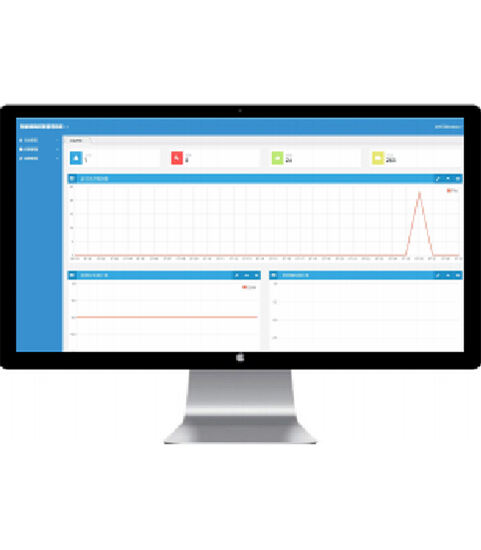
ပလက်ဖောင်းဟာ ဝန်ထမ်းတွေ၊ သော့တွေ၊ သော့တွေ၊ ခွင့်ပြုထားတဲ့ ဝန်ထမ်းတွေ ပိုင်ထားတဲ့ သော့တွေကို ဖွင့်ဖို့နဲ့ ပိတ်ဖို့ ခွင့်ပြုချက်တွေကို ဗဟိုပြု စီမံခန့်ခွဲပါတယ်။ ၎င်းဟာ သော့ချက် အချက်အလက်များနဲ့ သော့တွေကို ဖွင့်တာနဲ့ ပိတ်ခြင်းဆိုင်ရာ မှတ်တမ်းတွေကို အချိန်နဲ့တပြေးညီ ဖတ်ပါတယ်။ စာရင်းအင်းဆိုင်ရာ ဆန်းစစ်မှုနဲ့ စောင့်ကြည့်မှုအတွက် ဒေတာကြီးတွေကို မြင်ကွင်းထဲ ထည့်သွင်းပေးခြင်း။ -
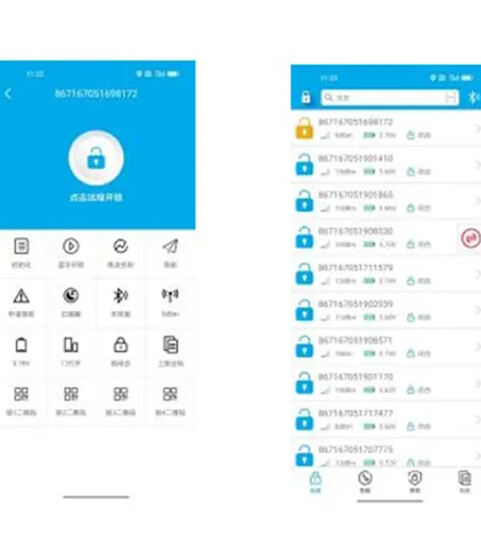
မိုဘိုင်းဖုန်း မီနီပရိုဂရမ်
သော့ထိန်းချုပ်ရေးနှင့် နေရာချထားခြင်း၊ တာဝန်များကို လျှောက်ထားခြင်း သို့မဟုတ် လက်ခံခြင်း၊ တာဝန်များကို လုပ်ဆောင်ခြင်း၊ ပုံမှန်မဟုတ်မှုများကို အစီရင်ခံခြင်း၊ စစ်ဆေးခြင်း၊ အတည်ပြုခြင်း၊ စောင့်ကြည့်ခြင်းနှင့် စာရင်းအင်းဒေတာ စသည်တို့ကဲ့သို့သော လုပ်ဆောင်ချက်များ။ -
Intelligent NB Iot အီလက်ထရောနစ် သော့
ရုပ်ပိုင်းဆိုင်ရာ ဉာဏ်ရည်ရှိတဲ့ သော့၊ အာဏာ၊ အချိန်နဲ့ ဝန်ထမ်းတွေအရ ပလက်ဖောင်းတာဝန်တွေရယူခြင်း၊ အခန်းတွင်းက လုပ်ဆောင်မှု မှတ်တမ်းတွေကို ပိတ်ဖွင့်ခြင်းနဲ့ အလိုအလျောက် တင်ခြင်းပါ။ -
အီလက်ထရောနစ် ပိတ်တံ
အလုပ်မလုပ်သော၊ ရေကြည့်ခြင်းမှ ကန့်သတ်ထားသော၊ လှိုင်းယူခြင်းမှ ကန့်သတ်ထားသော နှင့် ဖျက်ဆီးခြင်းမှ ကန့်သတ်ထားသော။ လှောင်စီလင်ဒါ၏အဓိကပစ္စည်းများမှာ 304 အမျိုးသားမက်က်ဖြင့်ဖွဲ့စည်းထားသည်။ အီလက်ထရွန်စီလှောင်စီလင်ဒါတွင် အတွင်းပိုင်းတွင် ကန့်သတ်ခြင်းခิပ်နှင့် အီလက်ထရွန်ဘာသာရပ်ပါဝင်သည်၊ လှောင်အလုပ်သမားများကို အလိုလို လက်လှုပ်စွာ တွေ့ရှိနိုင်သည်။ လှောင်များ၏ မျိုးစိတ်နှင့် မှတ်တမ်းများသည် မျိုးစိတ်နှင့် အခြေအနေများအတွက် ကျွန်းစုံသည်။
ဖြေရှင်းချက်: ကုမ္ပဏီပိုင် မီးတောင်းစီးမှုပုံစံ
-
စနစ်အလုပ်အတွက် ဘုတ်
ပင်ပင်ပုံစံဖြင့် အရေးကြီးမှုကို ရှင်းလင်းစွာ ပြသထားသည်။ -
လှိုင်း ကိုင်တွယ်မှု
စာရင်းနှင့် မှပ်ပြင်ပုံစံများကို အသုံးပြု၍ လှောင်တစ်ခုချင်းကို ရှင်းလင်းစွာ မြင်သာစွာ ပြသထားသည်။ -
အဖွဲ့အစည်းကို မြှင့်တင်ခြင်း
ဖွဲ့စည်းပုံအဖွဲ့အစည်းကို မြှင့်တင်ခြင်း -
ဒေတာဖတ်ခြင်း
ခေါင်းထိုးကို ကာဒီဖီစ်သို့ ထား၍ ဒေတာကို လွယ်ကူစွာ ဖတ်ရယူနိုင်သည်။ -
ပိုင်ဆိုင်ရာ ထုတ်ကုန်မenedžment
စီးရီးတစ်ခုစီအတွက် ဖြေဆိုခွင့်ပြုချက်နှင့် အချိန်လိုက်နာကို သတ်မှတ်ပြီး ထုတ်ယူခြင်းနှင့် ပြန်လည်ပေးဆောင်ရွက်ခြင်းအတွက် ကာလကို သတ်မှတ်ပြီး အသုံးပြုသူများကို တူညီမျှသို့ ချိတ်ဆက်ပါသည်။ -
ပြောင်းလဲမှုများအကြောင်း မှတ်တမ်း
ဖြေဆိုခြင်းနှင့် ပိတ်ဆိုင်ခြင်း၏ မှတ်တမ်းများသည် ရှင်းလင်းသော အခါများတွင် မြင်ရပါသည်။
ဖြေရှင်းချက်: NB-IOT Key

1.ကိုယ်ပိုင်အမှတ်အသားကို အရေးယူခြင်း
သော့သည် အသုံးပြုသူ၏ ကိုယ်ပိုင်အမှတ်အသားကို 岠ရောက်စွာ အရေးယူနိုင်ပြီး ပျက်စီးလိုက်ပြီး မှန်မှုမရှိသော ပြန်လည်ဖြေဆိုခြင်းနှင့် မှန်မှုမရှိသော ဖြေဆိုခြင်းကို ကန့်သတ်ပြီး သော့ပိုင်ခွင့်ရှင်၏ အခွင့်အရေးများကို ကာကွယ်ပေးသည်။
2.မှတ်တမ်းရိုက်ထားခြင်း လုပ်ဆောင်ခြင်း
အိတ်လိုင်းသော့ကိုယ်တိုင် အလုပ်လုပ်သူအချက်အလက်များ၊ ပိတ်ဖွင့်လုပ်ဆောင်ခြင်း၏ အစအဆုံးအချိန်များနှင့် ပိတ်ဆိုင်ခြင်းအကြောင်းအချက်အလက်များကို မှတ်တမ်းရိုက်ထားနိုင်သည်။
3.ဝေရှိုင်းပို့ခြင်း
NB-IoT ဆိုင်ရာပေးချူးမှုနှင့် Bluetooth ဆိုင်ရာပေးချူးမှုကိုသုံး၍ အလွယ်တကူ လှိုင်းပိတ်ဖွင့်ခြင်းအကြောင်းကို လျှော်လွှာတစ်ခုတွင် လှိုင်းပိတ်ဖွင့်ခြင်းအကြောင်းကို လှိုင်းဖွင့်ခြင်းကို ထိုးဝေနိုင်သည် သို့မဟုတ် အလှော်လွှာတွင် လှိုင်းပိတ်ဖွင့်ခြင်းကို အကိုင်းအကားဖြင့် လုပ်ဆောင်နိုင်သည်။
4.ခေါင်းထိုးအားခံရာမှာ
ခေါင်းထိုးက ပျောက်ဆုံးလျှင် အောက်ပါဖြေရှင်းချက်များရှိပါသည်-
1. ခေါင်းထိုးအတွက်ခွင့်ပြုချက်ကို လုပ်ငန်းခွင့်ပေးမှုပုံမှာ ဖယ်ရှားနိုင်သည်။
2. ခေါင်းထိုးကို လုပ်ငန်းခွင့်ပေးမှုပုံမှာ ဖယ်ရှားနိုင်သည်။
ဖြေရှင်းချက်: ပက်ဆိုင်ရှင်းလှုပ်ရှားသော လှိုင်းပိတ်ဖွင့်ခြင်း

ပညာရေးလုပ်ဆောင်ချက်များ
1、ပညာရေးဖွင့်ရန်အားလုံးကို ဖယ်ရှားခြင်း: ဒီဂျစတာကုဒ်ပြုခြင်းနည်းပညာနှင့် အကိုင်းအကားဆောင်သော ဆိုင်ရာပေးချူးမှုကို အသုံးပြုသည်;
2、မတူညီသော အချိုးအစားမရှိ: 64*8-ဂဏန်းကုဒ်၊ အချိုးအစားသည် သုညဖြစ်သည်;
3、လှိုင်းပိတ်ဖွင့်ခြင်းမှတ်တမ်းများရှိပြီး လှိုင်းပိတ်ဖွင့်ခြင်းကို ခေါင်းထိုးဖြင့်သာ လုပ်ဆောင်နိုင်သည်;
4、လှိုင်စက်သည် 22 ခုများစွာအတွက် (ဖွင့်ရန်၊ ပိတ်ရန်၊ စစ်ဆေးရန် စသည်) လုပ်ငန်းများ၏ လုပ်ငန်းမှတ်တမ်းများကို ထိုးဆောင်ထားသည်။
နည်းပညာ အတိုင်းအတာများ
1、လှိုင်ခုံ၏အဓိကပစ္စည်း: 304 ကြေးရောင်းမက်ဆယ်
2、ဗိုလ်တော်: 3V - 5.5V
3、အလုပ်လုပ်နေသည့်အပူချိန်: -40~80℃
4、အလုပ်လုပ်နေသည့်အရေပြား: 20% - 98%
5、ဖွင့်ပိတ်သည့်ကြိမ်နှုန်း: 300,000 ကြိမ်
6、ထိုးဆောင်နိုင်သော လုပ်ငန်းမှတ်တမ်းများ: 22 ခု
7、ကာကွယ်အဆင့် IP67
ဖြေရှင်းချက်: Rim lock

1.တေးဝိုင်းလုပ်ဆောင်ချက်များ
1、ပညာရေးဖွင့်ရန်အားလုံးကို ဖယ်ရှားခြင်း: ဒီဂျစတာကုဒ်ပြုခြင်းနည်းပညာနှင့် အကိုင်းအကားဆောင်သော ဆိုင်ရာပေးချူးမှုကို အသုံးပြုသည်;
2、မတူညီသော အချိုးအစားမရှိ: 64*8-ဂဏန်းကုဒ်၊ အချိုးအစားသည် သုညဖြစ်သည်;
3、လှိုင်းပိတ်ဖွင့်ခြင်းမှတ်တမ်းများရှိပြီး လှိုင်းပိတ်ဖွင့်ခြင်းကို ခေါင်းထိုးဖြင့်သာ လုပ်ဆောင်နိုင်သည်;
4、လှိုင်စက်သည် 22 ခုများစွာအတွက် (ဖွင့်ရန်၊ ပိတ်ရန်၊ စစ်ဆေးရန် စသည်) လုပ်ငန်းများ၏ လုပ်ငန်းမှတ်တမ်းများကို ထိုးဆောင်ထားသည်။
၂. teknical parameters
၁၊ lock body main material: 304 SUS
2、ဗိုလ်တော်: 3V - 5.5V
3、အလုပ်လုပ်နေသည့်အပူချိန်: -40~80℃
4、အလုပ်လုပ်နေသည့်အရေပြား: 20% - 98%
5、ဖွင့်ပိတ်သည့်ကြိမ်နှုန်း: 300,000 ကြိမ်
6、ထိုးဆောင်နိုင်သော လုပ်ငန်းမှတ်တမ်းများ: 22 ခု
7、ကာကွယ်အဆင့် IP67
၃. scene description:
တံတားရှိ အပြန်အလှန်လမ်းကြောင်းတွင် အသုံးပြုသည်။
အပြင်မှ ထောင်မှုရှိ electronic key ဖြင့် lock ကို unlock လိုက်ရန်ဖြစ်သည်။
အခြားအခါမှာ အတွင်းရှိ knob ကို လှည့်လိုက်ရင် lock ကို ဖွင့်ရန်လိုအပ်သည်။
Solution: phone mini program
လွယ်ကူသည် နှင့် မျှဝေသည်
Install မလိုပါ ဘဲ မိုဘိုင်းဖုန်းများအမျိုးအစားများအတွက် ကောင်းသည်
Task application
စစ်ဆေးမှုအခြေပြေအရ တာဝန်လုပ်ငန်းကို စတင်ရန်。
ကျွန်တော်၏ ကိရိယာများ
အလုပ်သမားများ၏ ထိန်းသိမ်းထားသော ကိရိယာများကို ပင်မဖွဲ့ဖြင့် ပоказထုတ်ယူပါသည်
လုပ်ဆောင်မှု တမ်းပလိတ်များ
လောက်များ၏ လုပ်ဆောင်မှု လုပ်ငန်းမျဉ်းများကို ရှင်းလင်းစွာ 示ပါသည်။
ထုတ်ကုန်အကျိုးကျေးဇူးများ
-
လုပ်ဆောင်ချက်စီမံခန့်ခွဲမှု
နေရာချိုးဖော် လုပ်ဆောင်မှုအတွက် လောက်ဖွေ့ချိန်၊ ကာလနှင့် လုပ်ဆောင်မှုအာဏာကို နေရာချိုးဖော်လုပ်ဆောင်မှုအတိုင်း အလိုအလျောက် ဖွေ့ချိန်အာဏာနှင့် အလိုအလျောက် အထိန်းပြုပါသည်။ -
လူသားများ စီမံခန့်ခွဲရေး
စနစ်မှူးများနှင့် နေရာချိုးဖော်လုပ်ဆောင်သူများ၏ အချက်အလက်များကို စီမံခန့်ခွဲပြီး အာဏာကို ဆောင်ရွက်ပါသည်။ -
လွှာစီမံခန့်ခွဲမှု
သုံးစွဲသူ မှတ်တမ်းများနှင့် လုပ်ဆောင်ချက်များကို ရှာဖွေ၊ ဂဏန်းထုတ်နှင့် အားထုတ်ပါ။ -
လှိုင်း ကိုင်တွယ်မှု
လক်ခုတ်အချိုးအစားများ၊ ဖိုင်များနှင့် လက်ခုတ်များ၏ အဆင့်အတန်းအရေးကြီးမှုကို ဆော့ဖ်ဝဲရှင်းပါ။ -
အာရုံစီးဆိုင်ရာ အချက်အလက်
လက်ခုတ်များနှင့် လုပ်ဆောင်ချက်များနှင့် ပတ်သက်သည့် အာရုံစိုက်မှတ်တမ်းကို ရှာဖွေပါ။ -
ပိုင်ဆိုင်ရာ ထုတ်ကုန်မenedžment
ခေါင်းဖိုင်များ၊ ခေါင်းအချိန်အခြေအနေများကို ဆော့ဖ်ဝဲရှင်းပါ။ လုပ်ဆောင်ချက်များကို ဒေါင်းလုတ်ပါ။
အဆင်ပြေမှု
-

ခေါင်းများကို အများအပြားရှိပြီး၊ ထောင်းချင်သည့် ခေါင်းကို ရှာဖွေခြင်းကိုလည်း ခက်ခဲသည်။
-

-
“One Key Pass” က အဖွင့်ဖြင့် လွယ်ကူသည်။
လုံခြုံရေး
-

ခေါင်းတစ်ခုပျောက်ဆုံးလျှင် အာမခံရာခံရမည်။ ခေါင်းတစ်ခုပျောက်ဆုံးလျှင် အားလုံးကို အစပြန်လုပ်ရန်လိုအပ်ပါသည်။
-

-
ခေါင်းထိုးက ပျောက်ဆုံးလျှင် အောက်ပါဖြေရှင်းချက်များရှိပါသည်-
1. ခေါင်းထိုးအတွက်ခွင့်ပြုချက်ကို လုပ်ငန်းခွင့်ပေးမှုပုံမှာ ဖယ်ရှားနိုင်သည်။
2. ခေါင်းထိုးကို လုပ်ငန်းခွင့်ပေးမှုပုံမှာ ဖယ်ရှားနိုင်သည်။
အားလုံးကို ပိုမိုကောင်းမွန်စေရန်
-

လက်လီမှတ်တမ်းအမှတ်အသားသည် လျှော့ချချို့မှုများရှိနိုင်ပြီး အဖွင့်အချိန်ကို လိုက်နာနှင့် ဆော့ဖ်ဝဲရှင်းခြင်းကို ခက်ခဲစေပါသည်။ လုပ်ဆောင်သူများကို ကိုင်တွယ်ရန်မရှိပါ။
-

-
၁. အလုပ်များ၊ အချိန်များနှင့် လူသည်များကို ခွဲထားပြီး ဝန်ထမ်းများအား စီမံကိန်းတစ်ခုချင်းစီတွင် လက်နက်ဖွင့်ရန် ပိတ်ရန် အ权တ်ပေးပါသည်။
၂. ပတ်သက်သော လုပ်ငန်းမျဉ်းများကို ကုမ္ပျူတာတွင် သိမ်းဆည်းထားပြီး တကယ်တော့ ကြည့်ရှုနိုင်ပြီး လွယ်ကူစွာ လိုင်စင်ရှာဖွေနိုင်ပါသည်။
မျှော်လင့်မှု
-

လက်နက်ဖွင့်ခဲ့သူ၊ ဖွင့်ခဲ့သည့်အချိန်ကို မသိရပါ။
-
-
လက်နက်ဖွင့်ခဲ့သူ၊ ဖွင့်ခဲ့သည့်အချိန်ကို ရှင်းရှင်းလင်းလင်း တွေ့ရပါသည်။
လုပ်ဆောင်ချက်များ၊ စစ်ဆေးခြင်းများ၊ လက်နက်အခြေအနေများစသည်တို့ကို အကွာအဝေးမှ လေ့လာနိုင်ပါသည်။
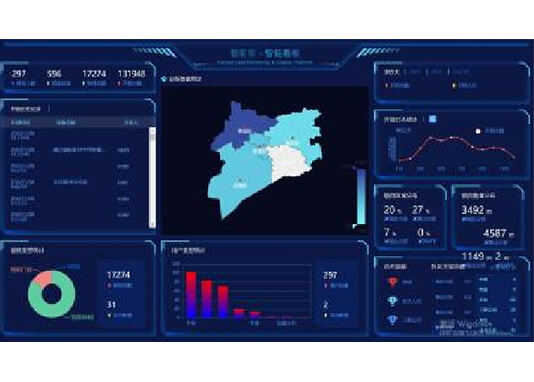
GPS အမှတ်အသားခြင်း / လမ်းညွှန်ခြင်း
-

ကာကွယ်ပုံများကို ဘာသာရေးလမ်းတွင် မျိုးမျိုးသော နေရာများတွင် ပို့ဆောင်ထားပါသည်။ လုပ်ဆောင်ခြင်းနှင့် မှတ်တမ်းစစ်ဆေးခြင်း၊ လုပ်ငန်းများကို လျှော့ချရန် အပြင်းအထန်များကို ရှာဖွေရန် အချိန်နှင့် အားကစားများလိုအပ်ပါသည်။
-

-
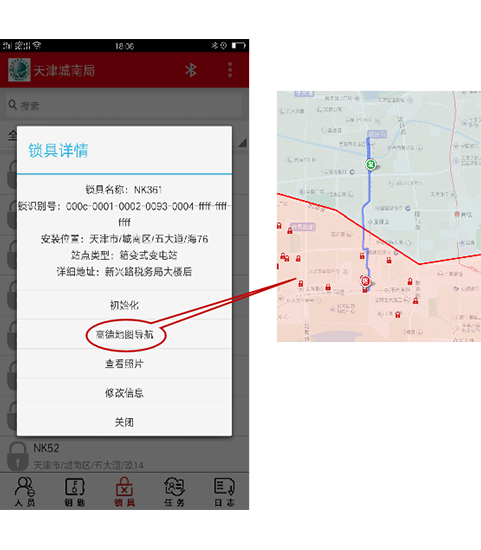
ဖုန်းမှတ်တမ်းအသေးစိတ်မှာ GPS လမ်းညွှန်ခြင်းအချိုးအစားရှိပြီး ဝန်ထမ်းများအား ဒီဇိုင်းထားသော နေရာသို့ ပထမဆုံးတွင် ရောက်ရန် အချိန်ကို လွယ်ကူစွာ သိမ်းဆည်းပြီး လုပ်ဆောင်မှုကို တိုးတက်စေပါသည်။
 EN
EN
 AR
AR
 BG
BG
 NL
NL
 FI
FI
 FR
FR
 DE
DE
 HI
HI
 IT
IT
 JA
JA
 KO
KO
 NO
NO
 PL
PL
 PT
PT
 RO
RO
 RU
RU
 ES
ES
 SV
SV
 CA
CA
 TL
TL
 ID
ID
 SR
SR
 UK
UK
 VI
VI
 TH
TH
 TR
TR
 FA
FA
 AF
AF
 MS
MS
 GA
GA
 CY
CY
 IS
IS
 AZ
AZ
 BN
BN
 LO
LO
 LA
LA
 SO
SO
 MY
MY
 KK
KK
 UZ
UZ