ferriviaria
Operatio iter ostium de summus celeritate praesidium saepe ferriviaria
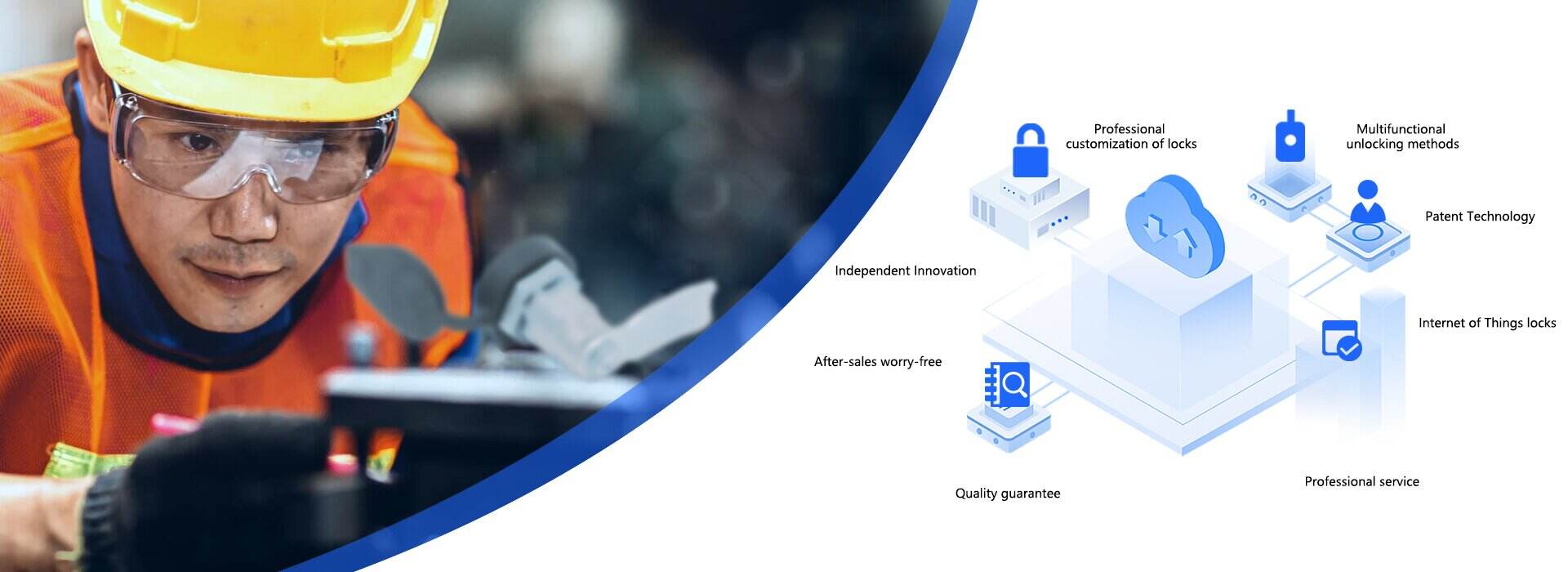
Elegantiarum procuratio solutionis

Background
Accidentia sepes ad tutelam pertinentia frequenter occurrunt et administratio fores operationis ignorari non potest.
-
Duo operarii constructionis rete praesidio ferriviarium ascenderunt et lineam ferriviariam sub instructione personae praesidentis intraverunt, et ibidem a vigilum stationem ferriviariam stationem ferriviariam Xiangyang Railway publica securitatis publicae Department of Xiangyang.
-
Intrantes per fracturam praesidii saepimentum ferriviarium contra legem et ambulans in linea ferriviaria, cum agmine currenti impactus, inde in mortes III.
Nunc et situ
Traditum ostium serae tutelae ferriviariae altae velocitatis saepes non habent functiones IMPERVITATIS, anti-curationis et anti-furti aperturae, nec desunt metus "mutandi ab extra ad intra et ab exposita in absconditum" capitis. officio.
Inspectiones regulares loco praevideri non possunt, et aerugo et damnum comarum nonnisi post res eveniunt cognoscuntur.
Project compage
-
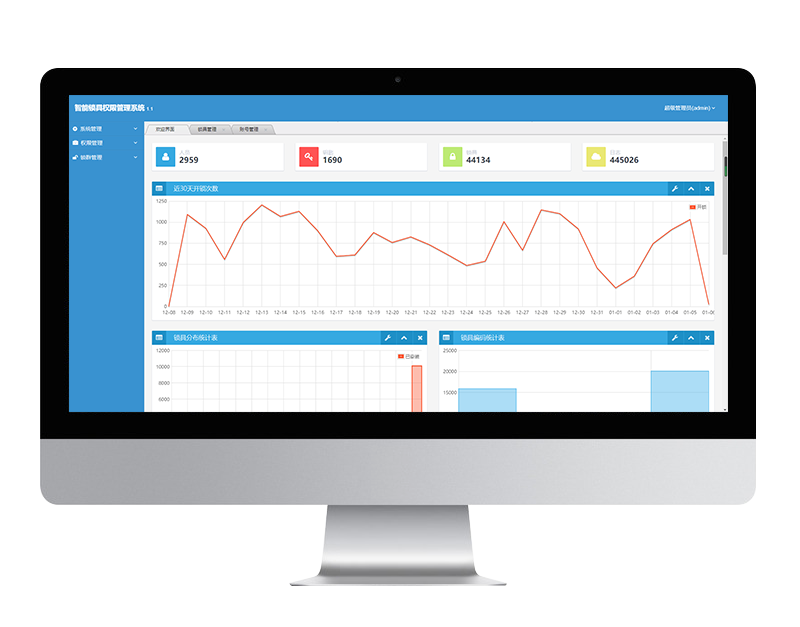
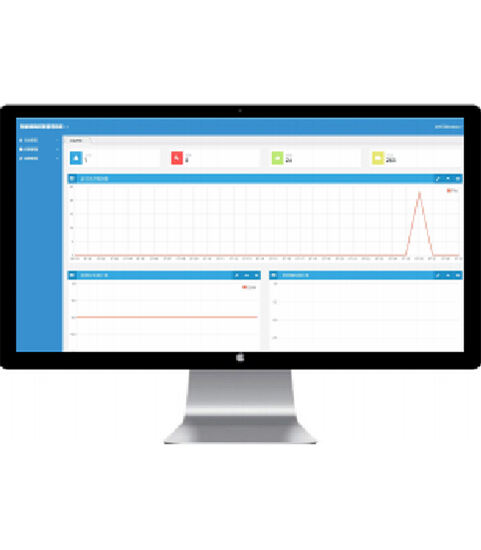
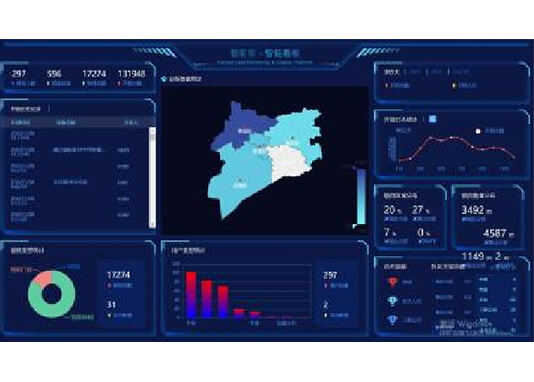
Clouds procuratio suggestus
Tribunal centraliter administrat personas, claves, seras et aperitiones et obeundas permissionum clavium ab auctoritate personarum tenentium. Legit informationes praecipuas et ad aperiendum et claudendum pertinentes monumenta cincinnorum in tempore reali. Magna visualisatio data pro statistica analysis et magna. -
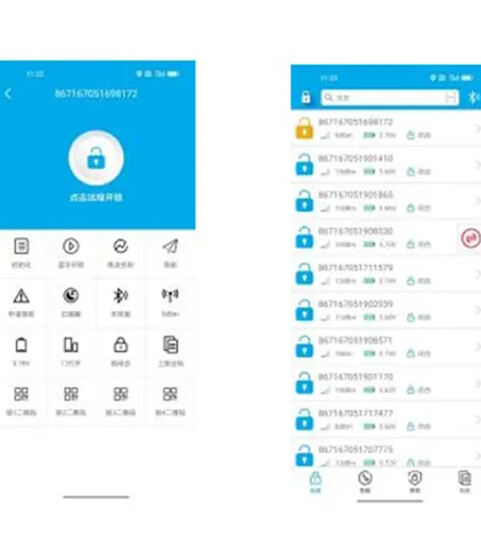
Mobile phone mini programma
Munera, ut seram administrationem ac positionem, munera applicandi vel recipiendi, munia exsequendi, renuntiationes abnormitates, inspiciendi, approbandi, vigilantiae, data statistica, etc. -
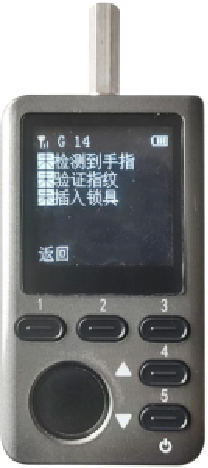
Intelligens NB Iot electronic clavis
Physica clavis intelligentis, officia tribunalia obtinens auctoritate, tempore et persona, aperiens ac automatice acta interne operandi imposuisti. -
Passivum electronic cincinno
Passivum, IMPERVIUS, anti-furtum, anti-curio. Materia principalis cylindri seriae est immaculata chalybe 304. Est electronica cylindrica cum chip in potestate et parte coegi electrici constructo, automatice cognoscens personas switch. Variae specificationes et specimina comarum variis missionibus apta sunt.
Solution: Cloudmanagement platform
-
Ratio opificinae
cum arbore structurae administratione claro visu. -
Cincinno procuratio
combining the list and map presentation method to make each lock clare visibilis -
administratione department
organization procuratio exstructa -
Legere notitia
Clavem pone in card issuer ut facile lege data. -
Key procuratio
permissio reserans et terminum singulis clavibus pone, tempus ponendi et recipiendi et retrahendi et ligandi usores simul. -
Switch records
Aperiendi et obandi monumenta visu patentia sunt.
Solutio: NB-IOT Key

1.Identity recognition
Clavis munus habet efficaciter cognoscendi identitatem utentis, quo minus clavem amissam et illicite reclusam duplicari prohibeat, et iura et utilitates clavium possessoris tueatur.
2.recording munus
Ipsa clavis intellegens notare potest operantis informationem, initium et finem tempus transitus seram operandi, et lock informationes, etc.
3.Transmissio remote
Usura NB-IoT communicationis et communicationis Bluetooth, statim potest clavum indicii switch imponere vel remotum monitorem cincinnorum operationum per telephonum mobile.
4.Clavis securitatis
Si clavis amittitur, sequentia solutiones praesto sunt:
1. Auctoritas praecipua in suggestu administratione deleri potest.
2. Clavis in suggestu administratione deleri potest.
Solutio: Passivum dolor cincinno

Munera technica
1、 Technicam reserationem: Adoptare digitales technologias coding ac technologiam communicationis encrypted;
2、 Nulla rate mutuus: 64*8 digiti coding, rate mutuus nulla est;
3、 Cum cincinnis monumentis transibit, cincinno switch clavi operandum est;
4° Sera cylindrica thesauros 22 operationes (recludens, densis, circuitus, etc.) tigna.
Technical parametri
1、Materia principale lock corpus: 304 immaculata chalybe
2、Voltage: 3V - 5.5V
3、Opus temperatus: -40~ 80℃
4、Opus humiditatem: XX% - XCVIII%
V, Switching temporibus: 5 times
6、Storable logs: 22 items
7、Protection level IP67
Solutio: Rim lock

1.Technical munera
1、 Technicam reserationem: Adoptare digitales technologias coding ac technologiam communicationis encrypted;
2、 Nulla rate mutuus: 64*8 digiti coding, rate mutuus nulla est;
3、 Cum cincinnis monumentis transibit, cincinno switch clavi operandum est;
4° Sera cylindrica thesauros 22 operationes (recludens, densis, circuitus, etc.) tigna.
2.Technical parametri
1、Locus corporis principalis materia: 304 SUS
2、Voltage: 3V - 5.5V
3、Opus temperatus: -40~ 80℃
4、Opus humiditatem: XX% - XCVIII%
V, Switching temporibus: 5 times
6、Storable logs: 22 items
7、Protection level IP67
3.Scene descriptio:
Usus est in transitu pontis subitis evacuatio.
Sera reserari cum clavis electronicis authenticis ab extra;
In subitis intus, nodi simpliciter gyrari ad recludam.
Solutio: Programma Phone mini
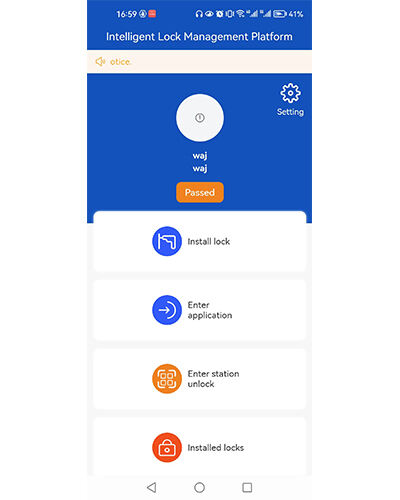
Commodum et ieiunium
Installatio nulla requiritur et apta est variis telephoniis gestabilibus generibus
Negotium application
Inchoare negotium applicationis processus secundum inspectionem status.
cogitationes meae
Ostendens esse machinas operariorum in ligno structurae
Operatio records
Operationem capillorum clare ostendunt.
productum commoda,
-
negotium procuratio
Area reserans, tempus et operandi auctoritatem constitue pro operatoribus in-site secundum necessitates operis siti, remotam reserationem et upgrade remotam. -
administratione curatores
Procuratio informationum rationum administratorum et operariorum in-site, et auctoritas constituens. -
iniuriarum procuratio
Visum, comitem et output auto-reprehendo tigna et operandi tigna. -
Cincinno procuratio
Circulus coetus informationes, cincinnorum fasciculorum, et hierarchica administratio capillorum. -
Terrorem informationes
Visum terrorem informationes ad seram et officia pertinentia. -
Key procuratio
Files clavis, administratione status, negotium download.
commodum
-

Est fasciculus magnus clavium, et rectum inveniendo etiam difficile problema est.
-

-
"Unus Key Est", conveniens reserans
Security
-

Si clavis amittitur, periculum securitatis est. Omnes claves reparari debent si una deperditur.
-

-
Si clavis amittitur, sequentia solutiones praesto sunt:
1. Auctoritas praecipua in suggestu administratione deleri potest.
2. Clavis in suggestu administratione deleri potest.
cultum
-

Adnotatio fabrilis manualis prona est ad densos, difficilis ad investigandum et ad tempus reserandum administrandum, et operarii inextinguibiles sunt.
-

-
1. Operas, tempus et personas assignare, et baculum in quolibet gradu commutare et permittere;
2. Relevant tigna in nube condita pro tempore reali inspicienti ac facili vestigando.
visualization
-

Homo qui seram reseravit / Tempus reserandi cognosci non potest.
-
-
Persona quae seram reseravit / Tempus reserationis visu clarum est.
Munus, inspectiones, status clausurae, etc. omnes possunt remotius viverra.
GPS positioning / navigation
-

Sepes tutelae per balneas variis locis disperguntur. In processibus operationis et conservationis inspectionis et instrumenti reparationis repentinae, multum temporis et industriae necessariae sunt ad certa loca invenienda.
-

-
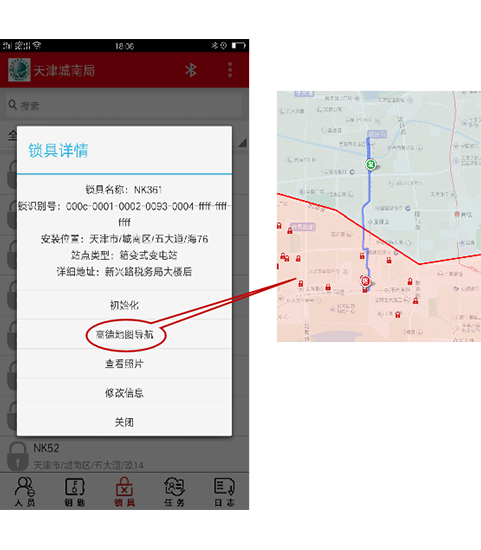
Telephonium mobile mini-programma GPS navigationis munus habet, quod permittit ut ad locum designatum primum perveniatur, maxime servato tempore ad inveniendam stationem et efficaciam laboris melioris.
 EN
EN
 AR
AR
 BG
BG
 NL
NL
 FI
FI
 FR
FR
 DE
DE
 HI
HI
 IT
IT
 JA
JA
 KO
KO
 NON
NON
 PL
PL
 PT
PT
 RO
RO
 RU
RU
 ES
ES
 SV
SV
 CA
CA
 TL
TL
 ID
ID
 SR
SR
 UK
UK
 VI
VI
 TH
TH
 TR
TR
 FA
FA
 AF
AF
 MS
MS
 GA
GA
 CY
CY
 IS
IS
 AZ
AZ
 BN
BN
 LO
LO
 LA
LA
 SO
SO
 MY
MY
 KK
KK
 UZ
UZ