
Overview
This document mainly describes the appearance and function of smart cylinder locks
Product Version
The product versions that correspond to this document are shown below.
| Product name | Product model | Product version |
| Smart bluetooth padlock | CRT-H100G | V100 |
Reader Object
This document (this guide) is intended for the following engineers:
●Installation Engineer
●Maintenance Engineer
All Rights Reserved.
Without the written permission of the company, no unit or individual may extract or copy part or all of the content of this document without authorization, and may not disseminate it in any form.
Note
Due to product version upgrades or other reasons, the content of this document will be updated from time to time. Unless otherwise agreed, this document is provided as a guide to use only and all statements, information and suggestions in this document do not constitute any express or implied warranty.
Product Overview
The smart lock contains a special chip inside, which can accept key commands to perform corresponding actions, and record unlocking and closing logs.
Product Appearance

Technology Parameters
| Lock body material | Copper&Stainless,steel&plastics |
| Whitelist num | 1000 sets |
| Black card num | 1000 sets |
| Unlock type | Card/Bluetooth/Mechanical lock core |
| Lock body material | SUS304/Copper |
| number of operations | 300000 |
| Unlock or lock status sensor | YES£ NOR |
| Encryption algorithm | AES/ECB |
| Number of logs | 500 |
| Working temperature | -10°C~80°C |
| Relative humidity | 20~100%RH |
| Protection class | IP68 |
| Working voltage | 2.2V - 3.7V DC |
| Standby current | <70uA |
| Unlocking current | <100mA |
| Sleep average current | <30uA |
| Battery | CR2(850mAh) |
| Full battery unlocking times | 5000 |
| Full battery standby time | 1.5 years |
Function Introduction
| Serial No. | Description |
| 1.Basic functions | 1. Avoiding technology opening: adopt digital coding technology and encrypted communication technology. 2. No mutual opening rate: 128-digit code, mutual opening rate is zero. 3. open lock record It can be managed and traced, and it can be used separately with the permission to open the lock,it can be customization. 4. There are 500 logs of storage operations (unlocking, closing, patrolling, etc.) in the lock cylinder. |
| 2.Unlock process | 1. Unlock via Cell phone First connect the phone to the lock via Bluetooth then send unlock command to lock,If it have permission ,then rotate the lock handle clockwise to unlock the lock and rotate it anticlockwise to close the lock. |
| 2. Unlock via Card First set the card ID to the whitelist in lock or set permission(include user,start time,cut-off time,lock id) into the card through cell phone,then take the card closer to the card swiping area. If it have permission ,then rotate the lock handle clockwise to unlock the lock and rotate it anticlockwise to close the lock. | |
| Unlock via Mechanical lock core First rotate the key 90 degrees clockwise,then rotate the lock handle clockwise to unlock the lock and rotate it anticlockwise to close the lock. |
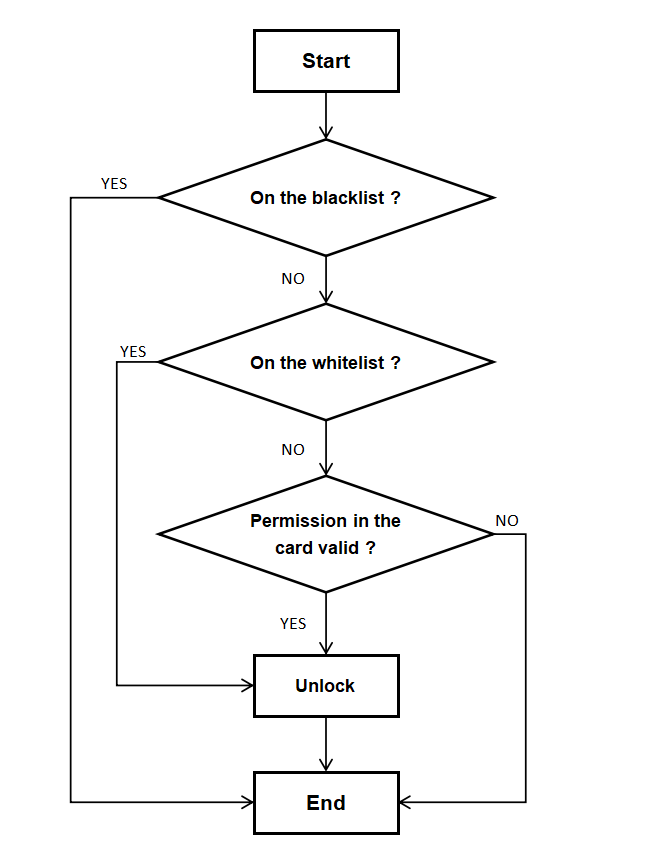
Priority Determination Of Card Swiping Permission

Copyright © Jiangsu Create Intelligent Technology Co., Ltd. All Rights Reserved - Privacy Policy